What are levels of disassociation?
We see market confusion when companies request or offer “non-attribution” of infrastructure. We have started socializing the idea that we need to classify levels of disassociation in relation to your origin point.
Level 0 = You or Origin connection
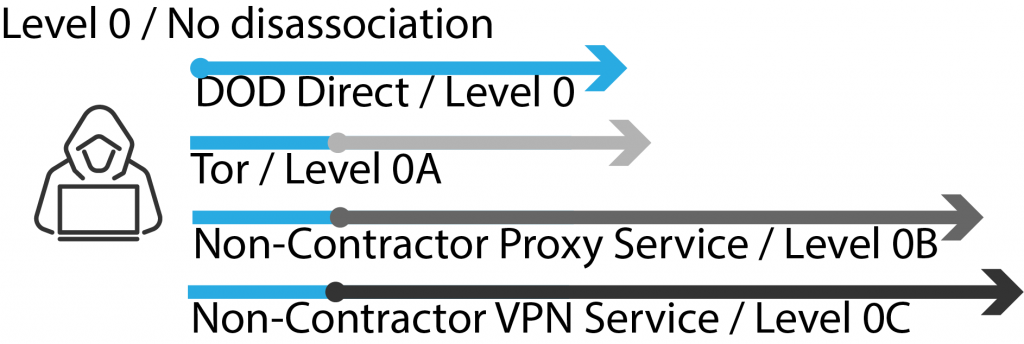
Level 1 = DOD affiliated contracting company

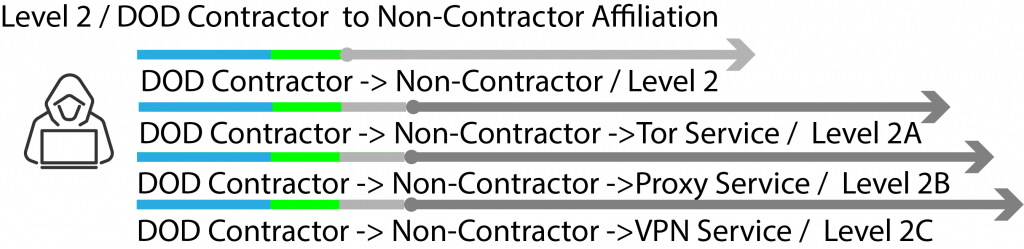
Level 2 = DOD affiliated contracting company to non-DOD affiliated company
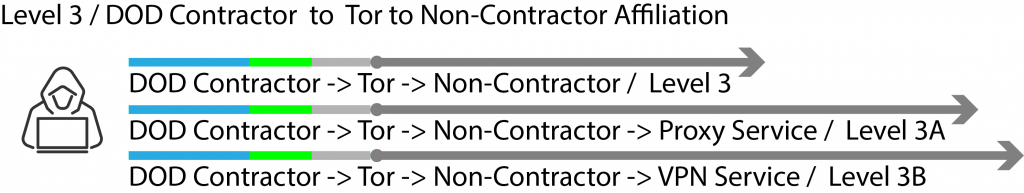
Level 3 = DOD affiliated contracting company to Tor to non-DOD affiliated company
Strengths/Weaknesses of well-known redirection services
Tor
Strengths: low barrier to entry, ease of use, possible to restrict originating country of requests.Weakness
Does not provide assurance of encrypted requests, does not guarantee delivery to intended end-point to due to proxy nature, does not guarantee speed and/or ability to maintain long-term sustained collection of desired materials.Tor+VPN
Strengths: basic non-attribution when combined with strategic acquisition process.Weakness
Speed and long-term sustained communications is not possible to ensure.VPN
Strengths: fast and reduced attribution to originator. Partial non-attribution when combined with strategic acquisition process.Weakness
Does not provide ability to quickly change IP space when VPN provider is identified. Does not protect against tampering from VPN providers that may become curious to current or future activities.Cloud Redirectors
Strengths: best value performance, scalability anywhere.Weakness
Provides disassociation up to contracting company vs attribution to DoD.FAQ
General
Pricing
Red Teams/SOC/Cyber Ranges
Compliance/Certifications/Security

